One of the greatest perks of my current job is the freedom to investigate any security topic of my choosing. This means that falling down the rabbit hole of threat intel is a common occurrence. The LNKR incident was my gateway into digital forensics, however this has uncovered a connection to another instance of malware called CopperStealer and evidence of what may be a pay-per-install network.
If you haven’t read my blog entry titled The LNKR Incident I advise that you go here and catch up before reading further.
Changes to policies in the Google Chrome store have made it more difficult for criminals to acquire legitimate browser extensions for malicious purposes. This has forced the operators of LNKR to adapt their strategies for deploying their malware. Enter CopperStealer.
Also known as Mingloa, CopperStealer is a credential and cookie stealer that comes equipped with a downloader. This makes the previous infection techniques used by the LNKR operators obsolete and greatly enhances their capabilities by enabling the deployment of other payloads without any user interaction. In fact, researchers have observed CopperStealer downloading versions of SmokeLoader, and PoisonIvy along side the LNKR malware.
According to Trend Micro’s investigation, CopperStealer infections were being distributed by way of malicious redirects that are embedded in the download links of cracked software sites such as keygenninja[.]com, piratewares[.]com, startcrack[.]com, and crackheap[.]net. On the surface, these websites offer pirated software and illegal product keys. Instead of the desired software the user ends up downloading a malicious executable… shocking, isn’t it?
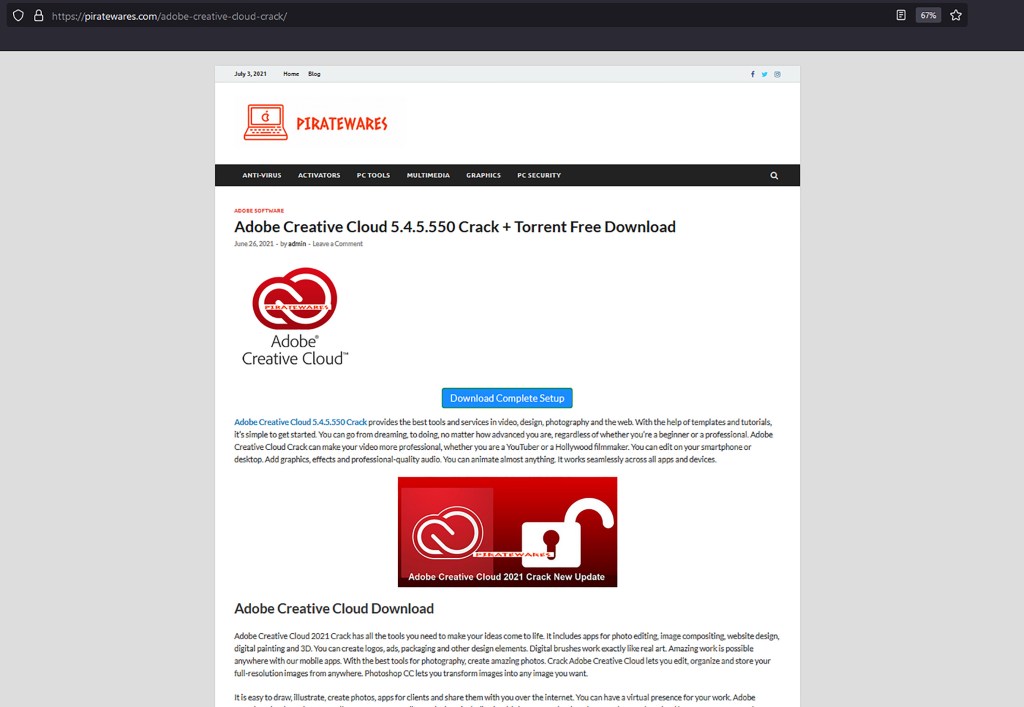
As of July 5, 2021, piratewares was the only site of those previously mentioned that was still functional and actively being updated. At the time of my investigation, their newest cracked offering was Windows 11. The problem with this is that Windows 11 wouldn’t be available for another 3 months and would be free upon release.
The case could be made that these sites are being victimized by malicious third parties. However, it’s worth noting that the piratewares website uses several dubious techniques to prevent researchers from analyzing the mechanics of its site.
Below is a list of the techniques I encountered.
1- The url within the Download button is obfuscated from revealing the link upon mouse-over. This is done by inserting the url within a href tag.
2- The user’s print screen button is temporarily turned into a hot-key while visiting the page. Instead of executing the usual screen-shot function, pushing the “prt sc” button leads the user back to their browser home page.
3- The mouse’s right-click button is disabled while visiting the page, likely to prevent using browser features such as “Inspect Element”.
Most of these anti-analysis features can be circumvented by disconnecting from the internet once the webpage has completed loading.
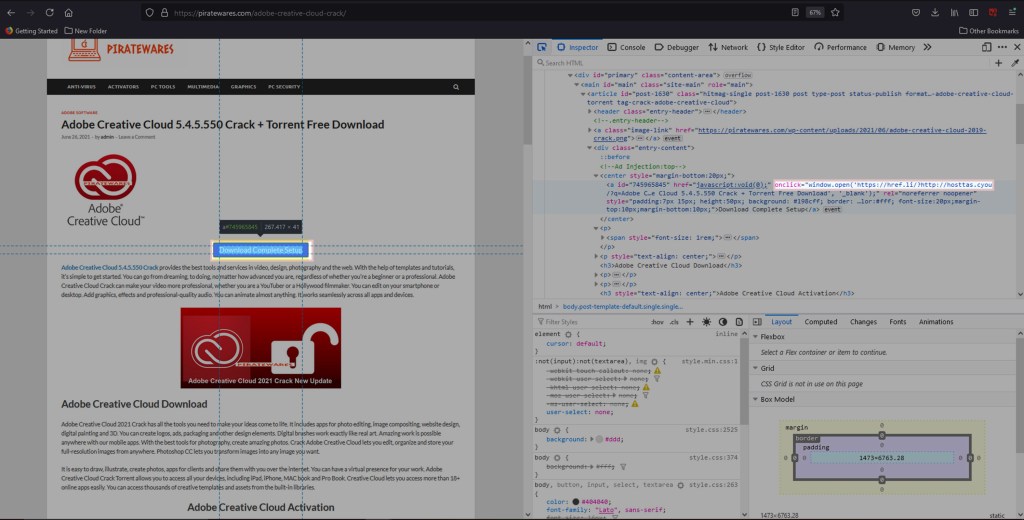
At first glance, the URL within the malicious “Download” button provides a link to the domain hosttas[.]cyou. A search of this domain in VirusTotal returns a rating of “Malicious”. Within 24 hours of my first inspection a new link to nri5host[.]xyz had taken its place. This domain name returned a rating of “Suspicious” in VirusTotal.
This sleight of hands could be interpreted a few ways. The first is that the URL’s are constantly being switched to avoid detection from antivirus blockers. The second is that piratewares is employed by a pay-per-install scheme. When the url lease has “expired” a new threat actor leases out the link. Both scenarios suggest that the operators of piratewares are knowingly involved in the infection of host systems in a part of a larger Malware as as Service (MaaS) network.
CopperStealer Workflow:
Disclaimer: The following analysis is based on research made publicly available by the authors. All relavant work is cited in the “Resources” section of this blog.
The first stage of infection begins when the user clicks a “Download” button on the malicious website. This begins a succession of redirections, resulting in the downloading of a password-protected zip archive. This contains both an executable payload and a text file with the required password.
The beginning of the second stage is marked by the installation of a decoy executable onto the victim’s system. This acts as a cover for the installation of the malicious payload. Once complete, CopperStealer then begins to create C2 server domains using a Domain Generation Algorithm (DGA) and begins performing communications using HTTP POST requests. These communications confirm the installation process, all data regarding the host environment, and the version installed.
It then performs a series of evasion techniques, terminating its routine if the system settings are in Chinese, run in a sandbox, or analyzed in a debugger.
If all system checks have passed the third stage begins. CopperStealer will proceed to implement two export functions. The first of which steals cookies and saved browser login credentials. The second export function is a browser extension installer capable of utilizing several malicious extensions. This would be the LNKR payload.
The malware then begins to exfiltrate harvested data, status updates, and download status updates to the C2 servers. Traffic is obfuscated using DES encryption and modified base64 encoding. The Domain Generated Algorithm can be reverse engineered, making it possible to predict the domains before they are activated. Knowing this, the writers hardcoded backup C2 server domains beginning with version 47.0.
CopperStealer then extracts a minimized P2P program called MiniThunder, created by Xunlei Networking Technologies Ltd. This is used to download the configuration for the second-stage binary. This returned configuration is encrypted and encoded and contains details regarding additional malware payloads.
Other Noteworthy Intel:
The type of data harvested is dependent upon the web service being targeted. For instance, if FaceBook is targeted CopperStealer collects the following information:
User ID cookie
Number of followers and friends
Facebook payment info
Credit card info
Linked Paypal accounts
Owned business advertising accounts
Facebook pages where the user has admin privileges
Facebook messenger cookie details, and when the FB page was created.
CopperStealer has evolved considerably, undergoing 80 major version updates between July of 2019 and March of 2021.
Between late January and May of 2021 CopperStealer was infecting up to 5,000 hosts per day, targeting the user credentials for Big Tech companies such as Facebook, Instagram, Apple, Amazon, Bing, Paypal, Google, Twitter and Tumblr.
CopperStealer is thought to be the work of Chinese threat actors due to similarities between its targeting and delivery methods and those of the Chinese malware family SilentFade. Both forms of malware will terminate if they recognize the host environment settings to be in Chinese. CopperStealer also employs the use of a downloader authored by a Chinese software company.
Summary
Investigating the LNKR infection on my college web page turned up evidence that the CopperStealer malware was the likely culprit behind the infection. After installing a malicious browser extension the LNKR malware is capable of scanning infected systems, exfiltrating reconnaissance data, redirecting search engine queries, and other basic adware functions. It also has a fairly ingenious method of fanning itself out to other hosts. CopperStealer has been seen downloading SmokeLoader and PoisonIvy payloads. Together, these act as a malware suite, providing threat actors with a tremendous amount of access to host systems. This is likely part of a larger Malware as a Service network.
Resources
